
Could You Be the Next 'Spoofing' Target?
Cybercrime is surging, and spoofing has become one of the sneakiest and most dangerous threats out there. From phony calls from your "bank" to emails that seem to come from trusted contacts, even the smartest people can fall for these traps. Want to stay one step ahead? Let's dive into the most common spoofing scams and learn how to protect your personal information from this rising menace.
What Is Spoofing?
Spoofing is when cybercriminals disguise themselves as a trusted source to gain access to personal information. This can happen through email, phone calls, websites, or even social media. The goal is often to steal sensitive data like passwords, credit card numbers, or personal identification information. Once your data is compromised, it can be used for identity theft, financial fraud, or worse. In an FBI report, people have reported to have lost more than $82 million to spoofing scams in 2021 alone.
Email Spoofing
Attackers fake the sender's email address to make it look like it comes from a trusted entity such as a colleague, bank, or service provider. The goal is often to trick the recipient into clicking malicious links, downloading harmful attachments, or providing sensitive information like login credentials. For example, an attacker might impersonate a legitimate company, sending an email that looks official but directs the user to a phishing website. To avoid falling victim to email spoofing from companies or brands, it's important to carefully examine the sender's address or reach out to your contact in person or by phone call to confirm that the message is real.
Text Message Spoofing
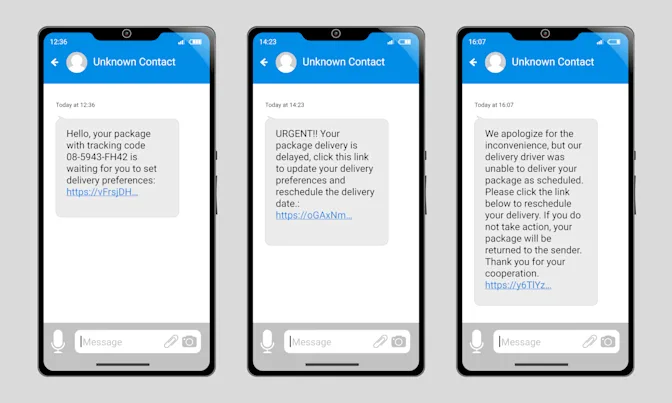
In text message spoofing, scammers manipulate their sender ID to appear as someone or an organization you trust, such as a family member, boss, or a company like Amazon® or your bank. Their aim is to deceive you into providing personal information or clicking a link that could infect your phone with malware. Unfortunately, creating spoofed text messages has become increasingly simple. If a scammer successfully impersonates your bank, you might unknowingly provide them with sensitive financial details. Additionally, victims can be tricked into sending money if they believe they are communicating with a family member or loved one.
Phone Spoofing
In this type of spoofing, cybercriminals manipulate the caller ID to make it seem like the call is coming from someone trustworthy, such as a bank or government agency. This technique is frequently used in scams, where the attacker pressures the victim into providing personal information. For instance, a scammer might pretend to be a bank representative warning you about fraudulent activity on your account, urging you to share sensitive details. To ensure the legitimacy of a call, reach out to the company directly before sharing any sensitive information, such as login credentials or credit card details.
Website Spoofing
Cybercriminals create fake websites that closely resemble legitimate ones, often using similar domain names to fool users. These websites are designed to capture login credentials, credit card numbers, or other personal information. These spoofed websites are often paired with email spoofing, where the email contains a link directing you to the fraudulent site. If you receive a suspicious email or text asking you to log in or verify details, don't click the link. Instead, open a new tab or use the official app to access the site directly.
IP Spoofing
This occurs when attackers disguise their own IP address to make it seem like the data they are sending comes from a trusted source. IP spoofing is often used in more sophisticated attacks, such as Distributed Denial of Service (DDoS) attacks, where the attacker floods a network with traffic using multiple spoofed IP addresses, overwhelming the system and causing it to shut down. Consider investing in a reliable antivirus program. If you accidentally click on a malicious link or attachment, a quality antivirus can detect the threat, block the download, and stop malware from infecting your device or network.
Spoofing is a real danger, but with the right know-how and a few smart moves, you can outsmart these attacks. Before clicking on suspicious links, opening strange emails, or sharing personal info over the phone, take a moment to verify who's really behind the message. Staying a step ahead of cybercriminals is easier than you think!
References: What Is Spoofing, and How Can You Spot It? | What is a spoofing attack?























